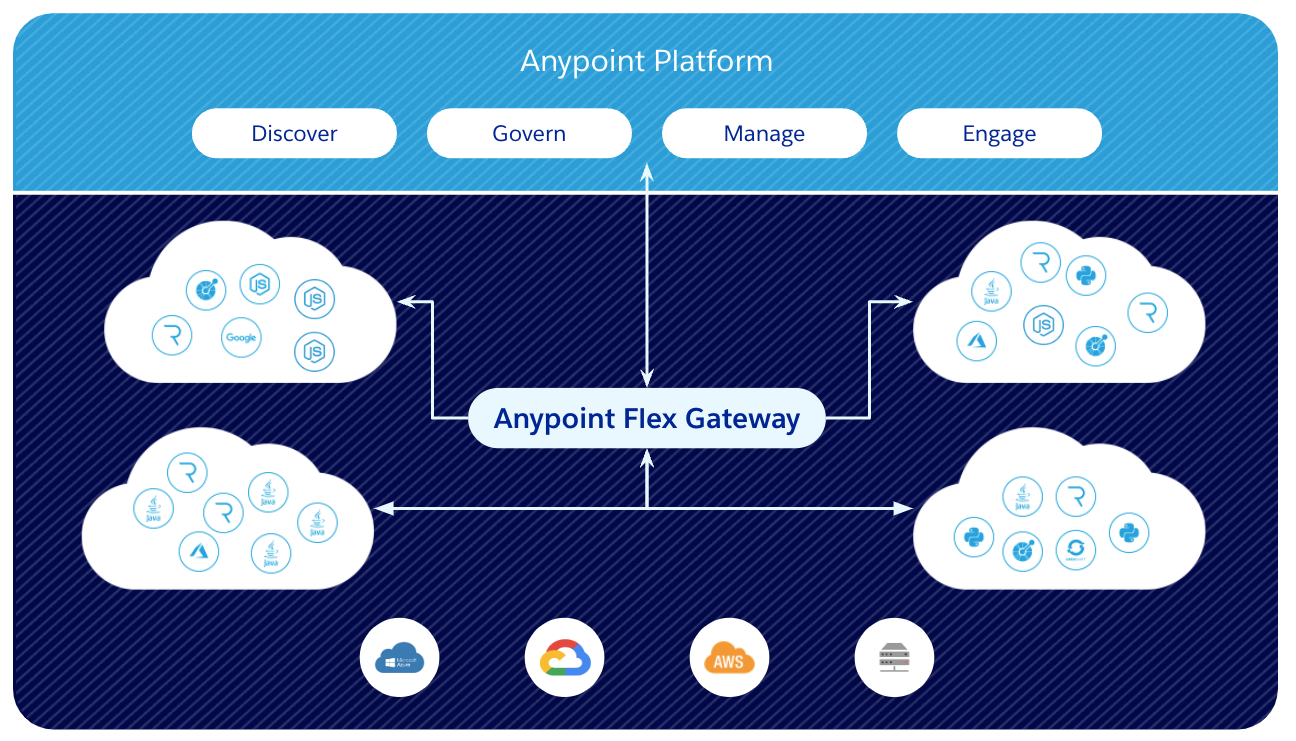
MuleSoft Flex Gateway is the new powerful API gateway designed for speed and security for non-mule APIs. It helps control and secure APIs across different environments with a variety of deployments - containers, on prem, cloud, kubernetes.



Notice we’re specifying the tag label for our image, to make sure we pull the last version available. But if you need a previous version you could specify it here.

Where:



Where:
If everything went well we should see all the resources under a newly created namespace running the command


From our Anypoint Platform, let’s go to API Manager and click on Add API > Add New API




With that, the details for our API would be: port 80 and Base path of our choice. Every API we add to our Flex Gateway will need to have a unique combination of base path and port (this is how our flew gateway will identify what API we’re referring to). Click Next







Prerequisites
Install K8s cluster
First we need a Kubernetes cluster up & running. It can be any K8s distribution - your own on prem cluster or a cloud-managed K8s such as AKS, GKE or EKS.
As we’ve seen in previous posts of these blogs, for testing purposes, a quick way to get our K8s cluster is using the K3s distribution. This distro allows us to spin up a K8s cluster with just one command.
For this tutorial, we’ll use an Ubuntu Server (version 24.04 LTS) running on an AWS EC2 instance. K3s, by default, comes with Traefik installed. For our example, we’ll install K3s with no ingress (our ingress will be Flex Gateway), so we’ll include in the installation command the option to disable Traefik.
Check out this post if you want to see in more detail the K3s installation.
Run the following command to install K3s:
As we’ve seen in previous posts of these blogs, for testing purposes, a quick way to get our K8s cluster is using the K3s distribution. This distro allows us to spin up a K8s cluster with just one command.
For this tutorial, we’ll use an Ubuntu Server (version 24.04 LTS) running on an AWS EC2 instance. K3s, by default, comes with Traefik installed. For our example, we’ll install K3s with no ingress (our ingress will be Flex Gateway), so we’ll include in the installation command the option to disable Traefik.
Check out this post if you want to see in more detail the K3s installation.
Run the following command to install K3s:
curl -sfL https://get.k3s.io | K3S_KUBECONFIG_MODE="644" INSTALL_K3S_VERSION=[K3s_VERSION] INSTALL_K3S_EXEC="--disable traefik --tls-san YOUR_PUBLIC_DNS_NAME" sh -s -In our example:
curl -sfL https://get.k3s.io | K3S_KUBECONFIG_MODE="644" INSTALL_K3S_VERSION=v1.31.1+k3s1 INSTALL_K3S_EXEC="--disable traefik --tls-san ec2-35-158-131-43.eu-central-1.compute.amazonaws.com" sh -s -Verify that K8s is up & running with
kubectl get nodes and verify that Traefik has not been installed (there should not be any Traefik pod). Run the command:kubectl get pods -n kube-systemOther Prerequisites
- We also need Docker installed. Check out this post on How to install Docker on Ubuntu Server
- We will need Helm for the Flex Gateway installation. Check out this post on How to install Helm
Installation of Flex Gateway
Go to your Anypoint Platform and select the Business Group and the environment where you’d like to create your Flex Gateway. Go to Runtime Manager and click Flex Gateway. Then click on the Add Gateway optionNext, we will see the different deployment options for Flex Gateway. We’ll choose Kubernetes. With that, we’ll see some instructions to follow to deploy Flex Gateway in our K8s cluster
Download the Flex Gateway image
Now, let’s head over to our K8s cluster. The first thing we need to do is to pull the Flex Gateway Docker image. For that run the following command:docker pull mulesoft/flex-gateway:latestCheck out the image is available in your Docker host:
docker imagesRegister the Flex Gateway in the Control Plane
Next, we’ll register our Flex Gateway. For that, we’ll run a container from the previous image and specify the registration command with the parameter values to connect to our anypoint org and environment. The output of the command will be a registration file so, before you run the command, create a new directory called flex-registration (or similar) and run the command from there.docker run --entrypoint flexctl -u $UID \
-v "$(pwd)":/registration mulesoft/flex-gateway \
registration create --organization=[YOUR_BUSINESS_GROUP_ID] \
--token=[YOUR_TOKEN] \
--output-directory=/registration \
--connected=true \
<gateway-name>
--entrypoint flexctl -u $UID- This flag allows us to override the default entrypoint defined in the docker image and run the flexctl command with the image.-v "$(pwd)":/registration- This options creates a bind mount mapping the directory from which we run the command to the /registration directory in the containermulesoft/flex-gateway- This is the image we’ve just downloaded in the previous step--organization- Specifies the BG ID where your Flex GW will be deployedtoken=[YOUR_TOKEN]- Specifies the access token to connect to your Anypoint org. You can generate the token using the Platform APIs or, much quicker, you can use the token generated in the Flex Gateway setup instructions we got in the first step. This is the quickest way to authenticate this operation but you can also use a Connected App or a Local Anypoint username and password.--output-directory=/registration- This option specifies the folder for the registration file of the output which is mapped to the current directory in the host via the bind mount.--connected=true- Specifies the mode for Flex Gateway (connected or local)[YOUR-GATEWAY-NAME]- A descriptive name for you flex gateway.
registration.yaml with the details for our new flex gateway to connect to the control planeGet back to Runtime Manager in our Anypoint Platform, we should now see in the Flex Gateways our new gateway in Disconnected status with 0 replicas.
Add Flex Gateway helm chart
Add and update the helm repository where the Flex Gateway chart is hosted.helm repo add flex-gateway https://flex-packages.anypoint.mulesoft.com/helm
helm repo upDeploy the Flex Gateway
Run the following command to deploy the Helm release using the registration file generated previouslyhelm -n flex-gateway upgrade -i --create-namespace --wait ingress flex-gateway/flex-gateway \
--set-file registration.content=registration.yaml \
--set gateway.mode=connected-n flex-gatewaySpecifies the namespace where the helm release will be installedupgrade -iIt tells Helm to install the release if it does not already exist.--create-namespaceCreates the namespace specified before if it does not existingressName of the Helm release--waitIt tells Helm to wait for all the resources in the chart to be in a ready state before marking the command as successful. This includes checking if Pods are running, Deployments are available, and Services have endpoints.flex-gateway/flex-gatewayName of the Helm Chart--set-file registration.content=registration.yamlSpecifies the yaml file where we stored the registration info we’ve got during the flex-gw registration--set gateway.mode=connectedSets the flex gateway deployment mode as connected
If everything went well we should see all the resources under a newly created namespace running the command
kubectl get all -n [YOUR_FGW_NAMESPACE]Head over to Runtime Manager and verify that our flex gateway is now in Connected status.
Test - Set up a Rate Limiting policy for a test API
Now let’s see if our new Flex Gateway works and can apply the policies we setup from API manager. For testing purposes, we’ll try to create an API instance to forward the incoming requests to our Flex Gateway to the Cat Facts free API (https://catfact.ninja/fact). We’ll try to set up a Rate Limiting policy so that we can control the number of requests sent in a period of time.From our Anypoint Platform, let’s go to API Manager and click on Add API > Add New API
Next, select Flex Gateway as runtime and pick up our new Flex Gateway from the list below and click Next
Then, Select an API from Exchange if you already have the asset in Exchange or Create new API. In our example, we’ll create a new API for the Cat Facts API (it’s a public free app for testing).
In the Downstream section, we need to provide the details of our Flex Gateway endpoint. In our case, when installing Flex Gateway as ingress, the enpoint is defined by the K8s Load Balancer service that was created during the installation. To see it clear, run the command:
kubectl get services -n flex-gatewayAs we can see, our Flex Gateway is exposed to ports 80 and 443 and the DNS name would be the Public DNS name that the Load Balancer service created. This depends on your K8s distribution. In AWS, for instance, you get an ALB with a public DNS name. In our example, with K3s, the public DNS would be the public hostname of our EC2 instance.
With that, the details for our API would be: port 80 and Base path of our choice. Every API we add to our Flex Gateway will need to have a unique combination of base path and port (this is how our flew gateway will identify what API we’re referring to). Click Next
In the Upstream section, we provide the details of the API we’re protecting and the rules to apply. In this post, we’ll keep it simple and forward all the traffic to the same URL. In our case, we’ll use the upstream URL
https://catfact.ninjaClick Next and then Save & Deploy. In a few seconds our API gateway would be ready. Now, to test it send a GET request to our Flex GW. In our case, it would be the public DNS of our EC2 instance where our Flex GW is running, on port 80 (the port of the ingress) and the relative path we want to access:
http://[FLEX_GW_PUBLIC_DNS]:80/factLastly, let’s try to apply a Rate Limiting policy to verify the policies engine works in our Flex Gateway. From API manager:
- click on the API instance we’ve just created
- click on Policies on the left panel
- Click on Add Policy
From the Quality of Service policies select Rate Limiting and click Next
Then, in the configuration of the policy set up 3 Requests per minute, just for the purpose of testing. Click Apply
Lastly, test the API instance again and send 4 requests. If the policy is working we should get a 429 error - too many requests.